The quantity of cyber strikes and information breaches in current years is shocking and it's easy to create a shopping list of companies that are home names that have been affected. Right here are simply a few instances. For the complete list, see our most significant information violations message. The Equifax cybercrime identification theft event impacted roughly 145.
In this instance, security concerns and answers were additionally endangered, boosting the threat of identity burglary. The breach was initially reported by Yahoo on December 14, 2016, as well as compelled all influenced users to alter passwords and also to reenter any kind of unencrypted protection questions as well as responses to make them secured in the future.
Getting My Cyber Security Company To Work
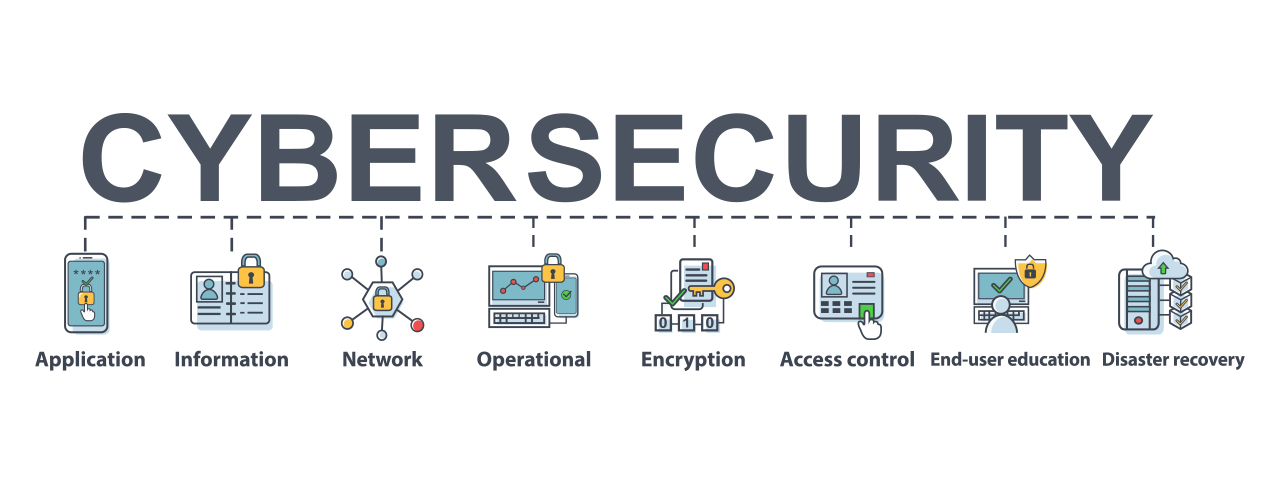
Cybersecurity is comparable to a bar or a club that weaves with each other many actions to secure itself as well as its customers. The most usual spyware generally records all user task in the tool where it is mounted. This leads to assailants figuring out sensitive details such as credit rating card details.

Cybersecurity is a huge umbrella that covers various safety components. Right here are the top ten finest techniques to comply with to make cybersecurity initiatives extra efficient.
Some Known Questions About Cyber Security Company.
This is either done by web solutions revealed by each remedy or by allowing logs to be legible among them. These solutions need to be able to expand in tandem with the organization and also with each various other. Misplacing the most up to date safety and security spots as well as updates is very easy with numerous security remedies, applications, systems, as well as gadgets involved - Cyber Security Company.
The even more critical the source being safeguarded, the extra constant the upgrade cycle requires to be. Update plans should be component of the preliminary cybersecurity strategy.
Cyber Security Company Things To Know Before You Buy
The National Cyber Safety Partnership suggests a top-down technique to cybersecurity, with company administration leading the cost throughout business procedures. By incorporating input from stakeholders at every level, more bases will be covered. Despite one of the most sophisticated cybersecurity tech in position, the obligation of safety and security most commonly drops on completion user.
An informed staff member navigate here base tends to enhance protection pose at every degree. It appears that regardless of the sector or size of an organization, cybersecurity is an advancing, necessary, and also non-negotiable process that expands with any type of company. To ensure that cybersecurity initiatives are heading in the best instructions, the majority of countries have governing bodies (National Cyber Safety Centre for the U.K., NIST for the U.S., and so on), which provide cybersecurity guidelines.
How Cyber Security Company can Save You Time, Stress, and Money.
They must be educated leaders that prioritize cybersecurity and personally demonstrate their dedication. Several directors know this, but still look for answers on exactly how to proceed. We carried out a survey to better recognize just how boards manage cybersecurity. We asked supervisors exactly how commonly cybersecurity was reviewed by the board as well as located that just 68% of respondents stated on a regular basis or continuously.
When it comes to comprehending the board's function, there were numerous alternatives. While 50% of respondents said there had actually been discussion of the board's function, there was no consensus regarding what that role need to be. Giving assistance to operating managers or C-level leaders was viewed as the board's function by 41% of respondents, participating in a tabletop workout (TTX) was discussed by 14% of the respondents, and also basic understanding or "standing by to react should the board be needed" was mentioned by 23% of Directors.
Cyber Security Company Things To Know Before You Get This
There are lots of structures readily available to assist an organization next page with their cybersecurity method. It is straightforward as well as provides execs and also directors a great structure for assuming via the essential facets of cybersecurity. It likewise has several levels of information that cyber professionals can use to set up controls, processes, and also treatments.
Cyber Security Company Fundamentals Explained
